Protect
Tackle the twin threats of piracy and sharing with an innovative suite of solutions to help you detect and disrupt piracy and drive subscribers back to your services.
Tackle the twin threats of piracy and sharing with an innovative suite of solutions to help you detect and disrupt piracy and drive subscribers back to your services.
Locate, monitor and analyse pirate sources and new players to understand the extent of your threat.
Detect leakage sources with robust, cost-efficient, studio-compliant forensic watermarking to protect your content investment.
Reduce credentials sharing. Accurately identify accounts that are sharing credentials and convert them to paying subscribers.
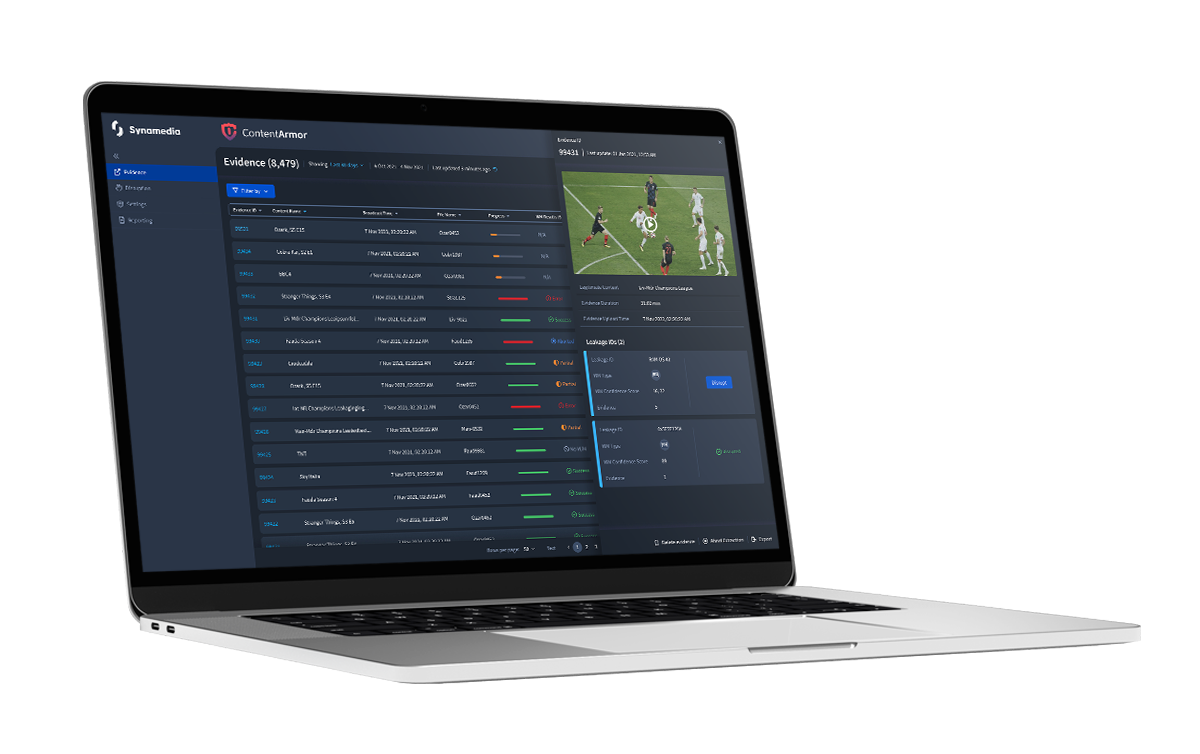
Forensic head-end watermarking to detect and identify malicious users, protecting content investments and preventing video piracy.
Discover moreSign up to Synamedia events and news